Passwords are the keys to our digital lives. They allow us to access our bank accounts, social media profiles, email accounts, and almost every other online presence. Over the years, passwords have evolved from simple four-digit PIN codes to complex, multi-character phrases that include uppercase and lowercase letters, numbers, and special characters. In today’s increasingly digital world, passwords are essential to protect our sensitive and confidential information from cybercriminals seeking to exploit them for personal gain.
However, despite their importance, passwords remain one of the major areas of compromise in our cybersecurity posture. Statistics from Finance Online show that 80% of data breaches involve compromised passwords – stolen or reused login information. Poor passwords cause 81% of company data breaches; the average person reuses the same password for multiple accounts – with 51% of people using the same passwords for both personal and work accounts, and the analysis of more than 15 billion passwords revealed the average password has eight characters or less.
Furthermore, according to a 2020 survey conducted by NordPass, the average person has around 100 passwords. Still, they only use about 25 regularly, and 59% create passwords containing their names or birthdays – a very bad idea. It is evident from these statistics that poor password hygiene results in outcomes that hurt organisations and individuals while also bolstering the importance of password security and how critical it is to safeguard our information.
World Password Day aims to raise awareness about the importance of password security and encourage people to protect their digital identities. The day is observed annually on the first Thursday of May. It serves as a reminder for individuals and organisations to protect themselves from cyber-attacks and data breaches by following password management best practices. In this article, we will discuss the threats to passwords, common mistakes people make, and recommended techniques for password security.
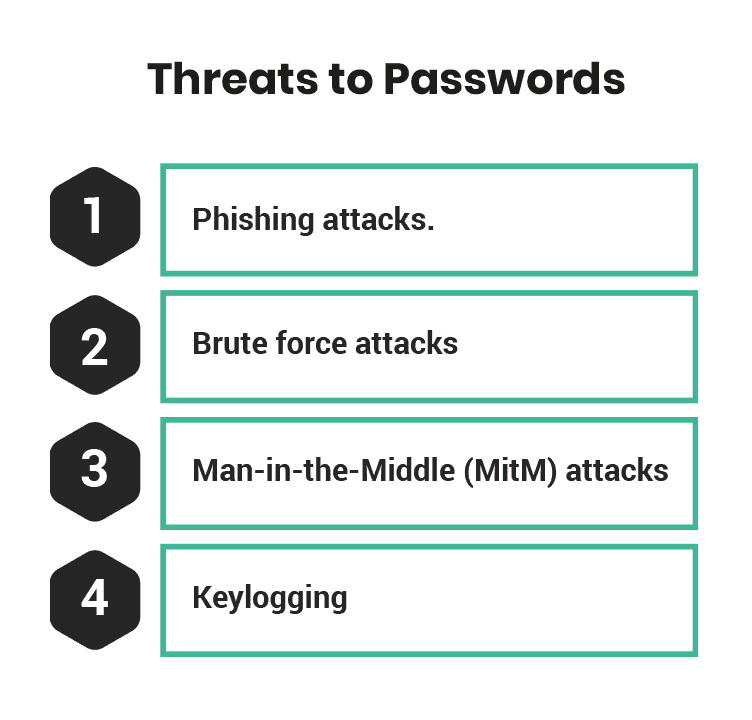
Threats to Passwords
While passwords are essential to protect sensitive information, they are very vulnerable to attack. The first-ever password attack happened in 1966, and it was as simple as printing out the list of passwords stored within the system. Yes, it was that simple. The master password list of MIT’s Compatible Time-Sharing System (CTSS) – a system designed to allow multiple users with different programs to interact nearly simultaneously, was printed by one of the PhD candidates, Allan Scherr. Allan figured he could print files by sending a simple system request. Nothing prevented him from printing the master password file, which gave him access to every user’s account, making him the first computer password hacker. This easy trick was the first in an evolution of techniques and tactics designed to perform password attacks. Modern password-stealing techniques include phishing, brute force, and Man-in-the-Middle attacks. They may also use software such as keyloggers to gain unauthorised account access. Password attacks are an ever-present threat, and I’ve compiled a list of the most prevalent password attacks you might face. After all, knowing what you’re up against is half the battle.
- Phishing attacks. A recent Anti-Phishing Working Group (APWG) survey found a record number of phishing attempts in Q3 2022 – 1,270,883 attempts, the worst quarter ever observed by APWG. Data from IRONSCALES research found that 81% of firms worldwide had seen a rise in email phishing attacks since March 2020. Here’s how phishing works, an attacker typically sends an email, text message, or social media message that looks legitimate and urges you to take immediate action, such as clicking on a link or downloading an attachment. However, the link or attachment may lead to a fake website or a malicious software program designed to steal sensitive information, such as passwords. Rather than trying to break into a system, the attacker relies on human error, naivete, ignorance, or greed to succeed.
- Brute force attacks. Unlike a phishing attack that relies on deception, a brute force attack attempts to gain unauthorised access to systems and applications through trial and error. A brute force attack systematically attempts to crack passwords by trying every possible combination of characters until the correct one is found. For example, if a password is six characters long and contains only lowercase letters, there are 308,915,776 combinations. A brute force attack would try every single one of these combinations until the correct password is discovered.
- Man-in-the-Middle (MitM) attacks. In a MitM attack, the attacker positions themselves between a user and the system they access. Here, the attacker seeks to capitalise on unencrypted communications or unsecured wireless connections, allowing the attacker to capture and intercept login credentials. This is why it is not advisable to use unknown public/free networks and insecure network protocols such as HTTP and telnet that transmit usernames and passwords in plaintext.
- Keylogging is often made possible by malicious software (malware). This malware captures every keystroke on a computer, including usernames, passwords, debit/credit card numbers, and other sensitive information. This information is then sent back to the attacker, enabling them to perpetrate identity theft and fraud. An effective anti-malware solution on computing devices is a good security measure to address this.
Ultimately, people are the weakest link in the cybersecurity chain. People make common mistakes such as using easily guessable passwords, reusing the same password for multiple accounts and sharing passwords with others. These mistakes make it easier for hackers to access sensitive information, leading to significant financial and reputational damage.
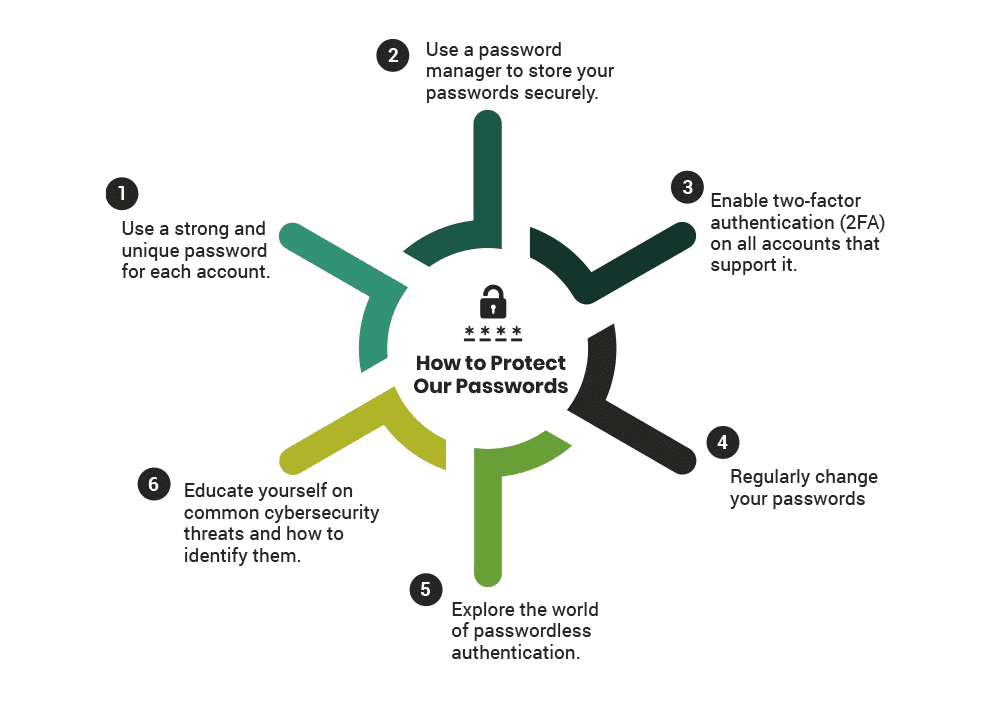
How to Protect Your Passwords
We can follow several best practices for password security to protect our sensitive information. These include:
- Use a strong and unique password for each account. A strong password includes uppercase and lowercase letters, numbers, and special characters. Avoid using personal information such as your name, birth date, or phone number. If you were to be a target, a dutiful attacker would do their homework – digging up as much information as possible about you, often from publicly available sources such as social media. Hence, details about you are often tried first when trying to break into your account. Your passwords should not be easily associated with your person to minimise the likelihood of a successful compromise.
- Use a password manager to store your passwords securely. A password manager generates and stores unique passwords for each account, making managing and remembering them easier. This prevents terrible password habits such as writing them on paper, saving them insecurely in Word documents and text files, and reusing the same password multiple times.
- Enable two-factor authentication (2FA) on all accounts that support it. There are three major forms of authentication – something you know (password, pin), something you have (token), and something you are (biometrics). Using at least any two of these is known as two-factor authentication. 2FA adds an extra layer of security by, for example, requiring users to provide a second form of authentication, such as a code sent via SMS or token, in addition to their password.
- Regularly change your passwords. Changing your passwords every three to six months reduces the risk of a password compromise. Your password must be changed immediately if your account has been associated with a data breach.
- Explore the world of passwordless authentication. Passwordless authentication is a method of verifying a user’s identity without requiring them to enter a password. Instead, the user provides evidence such as a fingerprint, proximity badge, or hardware token code. The FIDO (Fast Identity Online) Alliance is an open industry association developing and promoting passwordless authentication technologies. Their protocol – FIDO2, is based on public-key cryptography and uses a combination of hardware and software to enable secure authentication.
- Educate yourself on common cybersecurity threats and how to identify them. This includes phishing attacks, social engineering, and malware. Information security is everyone’s responsibility – stay aware and informed.
Password security is a critical aspect of data protection and privacy. With increasing cyber-attacks and data breaches, individuals and organisations must take password security seriously. Proactive measures such as using strong and unique passwords, two-factor authentication, regular password changes, and employee education on the importance of password security are crucial to securing and protecting our information from malicious actors. Remember, password security is a responsibility and a duty towards safeguarding our digital identities. It is vital to view passwords as we do toothbrushes: personal, unique, and to be changed regularly. By following best practices and staying informed on cybersecurity threats, we can keep our digital lives safe and secure.
At pcl., we offer end-user awareness and password security services to help organisations protect their sensitive information from cyber threats. We also enable organisations to build and maintain holistic information security systems based on best practice standards and frameworks and create synergy between security and business objectives, thereby facilitating sustainable business growth securely. Do contact us at cybersecurity@phillipsconsulting.net.
Written by:

Ikenna Ndukwe
Consultant