Imagine this; you have had a long day at work. It has been gloomy and stressful, and you are picturing yourself relaxing at home – taking a nap or watching a movie, maybe. These thoughts give the rest of your day a glimmer of light as you make your way home. Finally, you try to unlock your door at home, and it does not budge no matter how hard and how many times you twist and turn. You try another door, the same result. Upon further examination, you realise that the locks of your entries have been changed. Somehow, someway, an intruder was able to replace the locks of your door. On the threshold of one of the doors, you see a note that reads, “YOUR LOCKS HAVE BEEN CHANGED! YOU HAVE 6 HOURS TO PAY TO GET THE NEW KEYS.” Your day just got worse.
The scenario painted above describes how a ransomware attack works and how frustrating it can be for organisations and individuals that fall victim. On the back of a digitally disruptive post-covid era, the frequency of Ransomware attacks has been trending in the news in 2021. In fact, according to Cognyte – a global leader in security analytics, in the first half of 2021, the number of ransomware attacks nearly doubled, with the number of victims growing by almost 100%. You may have read of ransomware attacks on private and public organisations or perhaps have experienced it yourself.
What is Ransomware?
Ransomware is malicious software or malware that prevents an individual or organisation from accessing their systems or files and demands that a ransom, usually in a cryptocurrency, be paid to regain access. It is a growing problem and a frightening prospect to have all your data locked up until you pay up. During the infamous WannaCry ransomware attack of 2017 – the largest in history, approximately 200,000 victims from nearly 150 countries were asked to pay a ransom in Bitcoin.
In more recent times, the largest fuel pipeline in the United States – Colonial Pipeline, was forced to shut down operations and freeze information technology systems after being the victim of a ransomware attack in May 2021. Colonial Pipeline paid the hackers a $4.4 million ransom in Bitcoin. In June 2021, the world’s largest meat processing company – JBS, paid the equivalent of $11 million in Bitcoin to put an end to a ransomware attack. These reports show that the global impact of ransomware has reached new heights in 2021. These attacks not only fleece organisations of millions of dollars but also impact public lives. Cybercriminals are also expanding their targets, leaving no one safe from financial damage or reputation-crushing headlines.
How exactly does a cybercriminal execute a ransomware attack?
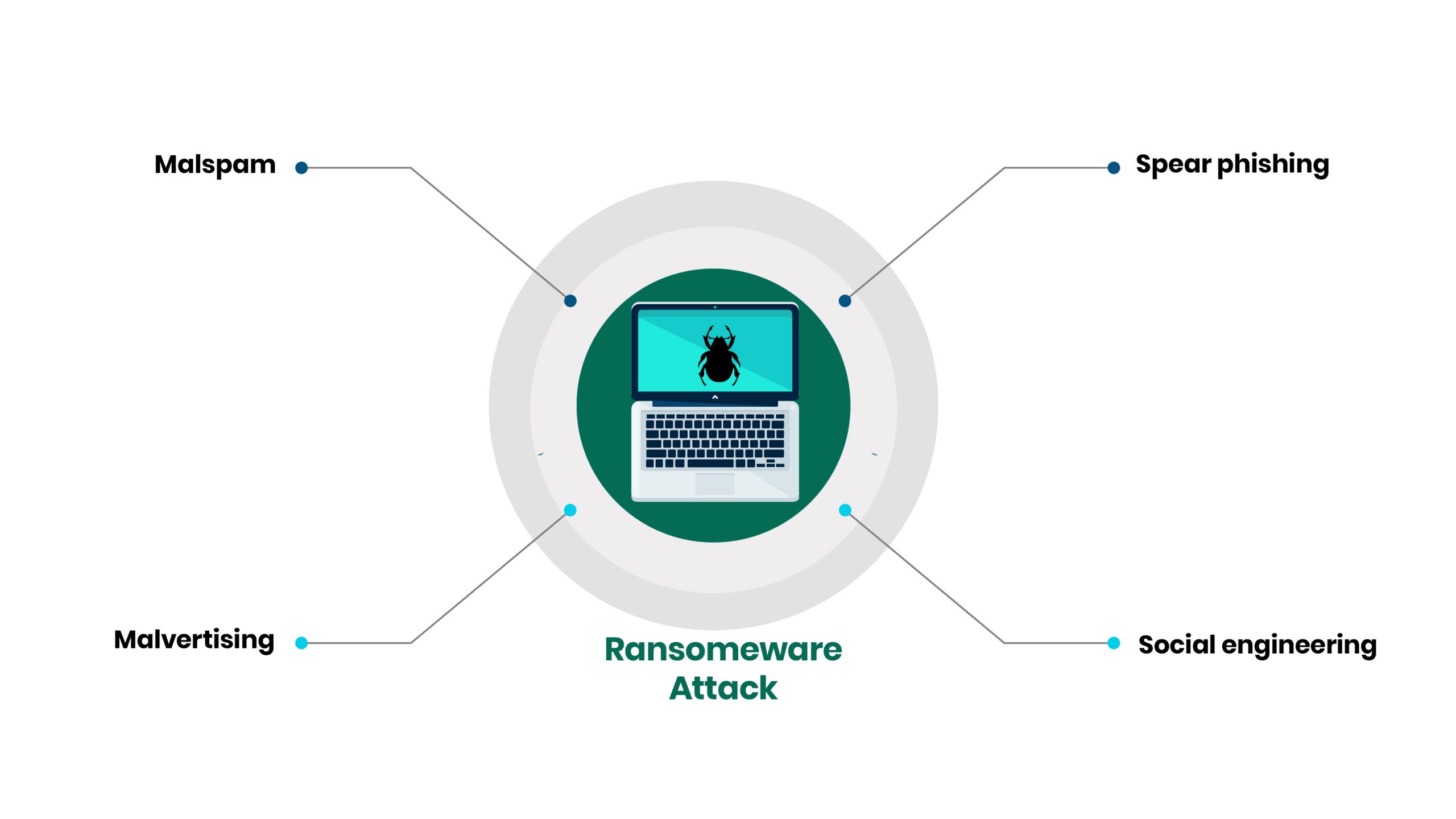
First, cybercriminals usually exploit a vulnerability or weakness to gain access to a system or network. Having such access enables the hacker to activate the malware needed to encrypt or lock up your systems and files. There are several ways that ransomware can infect your systems:
- Malspam: Some cybercriminals use spam, where emails with malicious attachment(s) are sent to as many people as possible, seeing who opens the attachment(s) and “takes the bait.” These mails could also contain links to malicious websites.
- Malvertising: This is using online advertising to distribute malware with little to no user interaction required. While browsing the web, ransomware can redirect users to malicious websites without clicking or interacting with an ad.
- Spear phishing: The sole purpose is to get inside the recipients’ heads and make them think the messages they’re responding to are legitimate – achieved due to personal touches designed to make them believe what they’re dealing with is a genuine individual or entity. These personal touches can be gotten from their social media accounts about their interests, places often visited, jobs, etc.
- Social engineering: Malspam, malvertising, and spear-phishing often do contain elements of social engineering. Cybercriminals can trick users into opening attachments or clicking links by appearing legitimate. This method is focused on “hacking the individual.”
Whichever way or method the cybercriminal uses to compromise your systems, the ransomware encrypts your files, and once they gain access, this prevents you from accessing them. A message is displayed demanding a ransom payment to restore your access.
The threat landscape in Africa
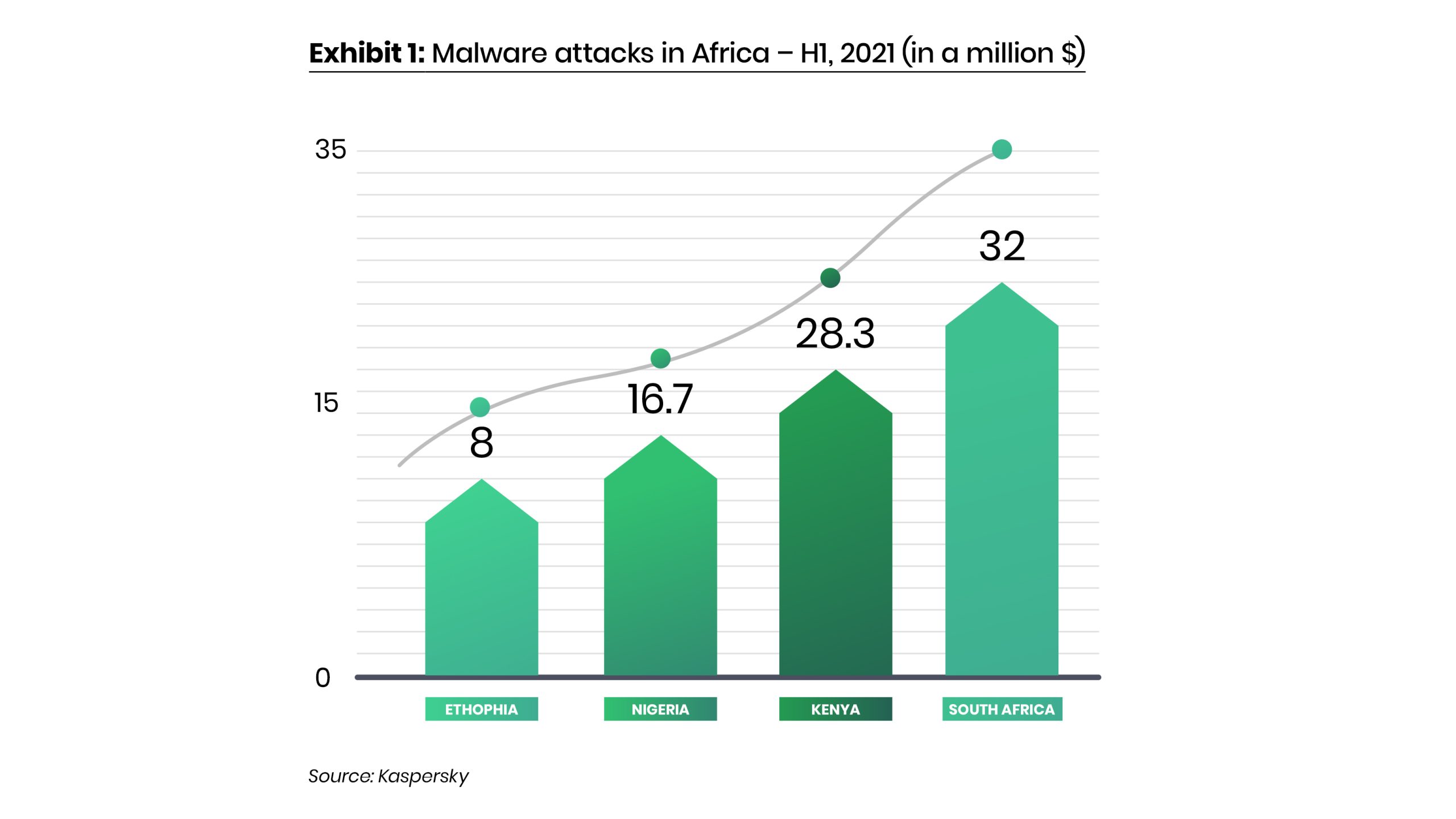
While the ransomware attacks that make the headlines are often based in developed countries, and Africa is not considered a focus area for the more advanced types of cybercriminal activity, the continent is not immune to these cyber risks. Considering the growth of digital transformation and increased remote working triggered by the COVID-19 pandemic, Africa is becoming an attractive target for cybercriminals looking to exploit a lack of end-user awareness and cybersecurity understanding. Kaspersky – a global leader in cybersecurity, reports that malware is rife across the continent, with various countries exhibiting strong growth across multiple malware types in 2021. In the first six months of 2021, as many as 85 million malware attacks, a 5% rise compared to the corresponding period in 2020, were detected in just four countries.
All countries except Kenya saw a relative growth of malware attacks. Compared to the previous year, Kenya’s number of attacks was down by 13%. South Africa and Ethiopia have seen an increase of 14% and 20%, respectively, with Nigeria seeing the most significant increase of 23%. These figures prove that cybercriminals are beginning to refocus their efforts to compromise corporate and consumer systems within Africa. Cybercriminals are working overtime, so organisations and individuals must take proactive steps to protect themselves and their assets.
How to insulate your business from ransomware
Based on these findings, the following best practices are recommended:
- Assume you will be the next victim. Ransomware remains highly widespread. No industry, country, or organisation size is immune from the risk. It is better to be prepared but not hit than the other way round.
- Make backups. Backups are the number 1 method organisations use to get their data back after an attack. Paying the ransom will only get you some of your data – an average of 65% of information is restored after the payment of ransom, according to a Sophos study, so you will need to depend on backups either way.
- Defence in depth. There is not a single control or safeguard that is 100% foolproof. Hence, multiple rules, implemented serially, will provide a greater level of protection assurance. Use layered protection to block attackers at as many points as possible across your environment.
- Combine anti-ransomware technology with human experts. The remedy to stopping ransomware is defence in depth that combines dedicated anti-ransomware technology and human-led threat hunting. While technology provides the scale and automation you need, human experts can best detect the tell-tale tactics, procedures, and techniques that indicate that a skilled attacker is attempting to get into your environment.
- Do not pay the ransom. While this is easier said than done, paying the ransom is ineffective to get your data back. If you do decide to pay, be sure to include in your cost/benefit analysis the expectation that the cybercriminals will restore, on average, only 65% of your data and files.
- Have a malware recovery plan. The best way to stop a cyberattack from turning into a complete breach is to prepare in advance, be proactive. Organisations that are victims of an attack often realise they could have prevented a lot of pain, cost, and disruption if they had an incident response plan in place.
But there is a lot more, and at pcl., we have got you covered. We help build and maintain cyber-resilient enterprises with various offerings cutting across people, technology, and processes to guide our clients as they navigate these disruptive times. Our approach involves understanding the context of your business environment, identifying internal and external factors and stakeholders that could influence your overall protection strategy, your business drivers – mission, vision, goals, and objectives, and the threats and risks that could prevent you from achieving those objectives. Our assessment methodologies incorporate both technical and non-technical approaches to strengthen your security posture holistically. Beyond assessments, we partner with you to navigate from your current state to the desired future state that will deliver the needed return on security investments. In addition, we offer technology consulting services and products from FinTech, Data Analytics, Standards & Compliance, and Training. Do reach out to us!
Protect yourself and your assets, do not be another statistic!
Written by:

Ikenna Ndukwe
Assistant Consultant