Africa experiences so many cyberattacks per second, with the perpetrators aiming at defrauding unsuspecting businesses or individuals using various vulnerability methods like phishing, social engineering, and many more. Among the different business sectors in the Nigerian economy, the financial industry has been the most affected by various cybercrimes through user and domain impersonation. Over the last two years, there has been a massive increase in user impersonation, with unsuspecting users getting defrauded of their life’s work. As productive as the remote/mobile technology model might be for financial institutions, it is essential to educate businesses on the need to have an end-to-end secured business process that protects their devices and work tools with models like the zero-trust model.
Zero-trust assumes that everyone who attempts to access a resource is a bad actor. As such, high-level access control is implemented to check the individual identity through conditional access with MFA. Applying conditional access policy is highly recommended; with the high rate of BEC scams prevalent worldwide, we see individuals and even IT professionals falling prey to BEC scams.
Simply put, the BEC scam is a business email compromise scam. It is a method where a bad actor deceives an unsuspecting individual or entity through email, acting as a legitimate entity to commit financial fraud.
A security-ready organisation understands the importance of having a solid security posture as this saves time, money, and the reputation of the company or individual and its interest. Today, the world swims in numerous cyberattacks, with IT specialists doing their best to salvage attack situations. However, there is a need to invest in cybersecurity as most organisations now depend on one cloud solution to meet their business goal and objectives.
User Education
End-user education plays a vital role in mitigating BEC scams and other cyberattacks as the cloud operates a security model known as a shared responsibility model. In this model, the cloud provider manages the infrastructure while you manage your data and how it is accessed. Therefore, end-users and SMEs must understand the risk associated with ignorance.
A simple task such as hovering your mouse on the email sender ID to confirm if it matches the sender’s address, looking out for wrong spellings and messages showing a sense of urgency, high impact, and high risk are simple ways to confirm BEC scams. Research has shown that messages could also be sent from telnet servers and coded in a way to deceive the simple task mentioned earlier on. Therefore, SMEs should endeavour to manage their messaging systems with available and efficient Pay-As-You-Use cloud solutions that can meet their budgets to aid continuity as these products should be able to filter connection requests, manage and administer messaging rules and policies, protect company data, and improve overall business security (secure score).
The banking and finance sectors are the most affected by deepfake elaborate phishing campaigns, mainly through emails; these emails carry embedded attachments that can be malware with a form of extension that can carry out RCE – remote code execution. Nigeria business experiences over 2000 cyber-attacks weekly according to business day. BEC takes the lead deployed with phishing tactics, as such emails might look legitimate if a proper check is not carried out to verify the authenticity of such emails.
Mitigation
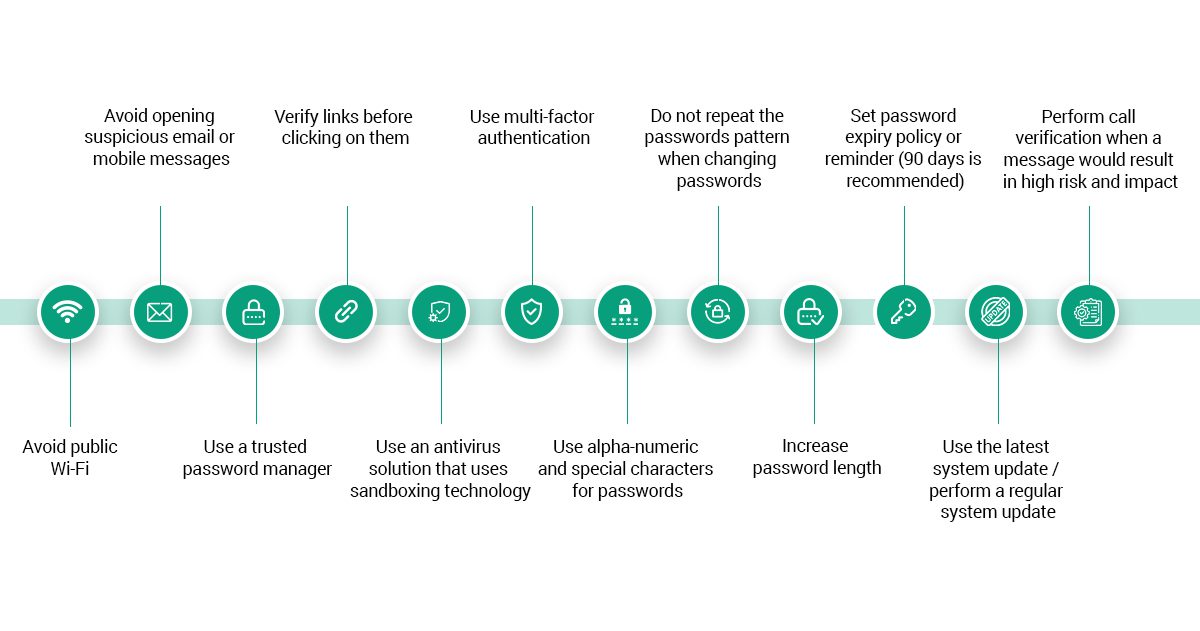
Humans find it easy to move toward the “known danger” than the “unknown safety”; however, it is essential to know that this unknown safety can be handled with proper awareness campaigns specifically tailored to equip users with the necessary best practices. Some of these best practices are outlined.
The above best practices are inexhaustive; however, the security model used by cloud providers is the “shared security model,” which implies that the cloud provider is accountable for some services and the customer is also responsible for some services. Two services cut across the cloud platform for the shared responsibility model: identity security and data security.
An excerpt from the Cloud security alliance states that “it’s important to understand that you and your cloud provider never share responsibility for a single aspect of security operations. The areas of ownership you Control are yours alone, and your provider does not dictate how you secure your systems”.
Therefore, SMEs should be able to conduct a complete compliance check-in which should be aligned with their business practices. Thus, the following must be carried out – risk assessment, network access control, application control, implement advanced threat protection, Implement firewalls and antivirus software, create a patch management schedule, monitor network traffic, build an incident response plan, implement a zero-trust security model across all business infrastructures.
Research has shown that due to various components transverse across humans and machines, there is no single way to protect your organisation one hundred per cent from cybercrime. Therefore, it is important to stay aware of any latest news related to your business operation. Most cloud solution providers have various communication channels used to inform their customers of current happenings, updates, or attacks related to service availability and to keep their customers that are outlined but not limited to CIO, CTO, SysAdmin, and relevant stakeholders abreast.
Any organisation that wants to mitigate any disaster should make sure they are security agile in tackling potential threats that might reduce their security posture via the mitigation processes outlined earlier. Also, most cloud providers are flexible for organisations to set up a hybrid system, which is another way cloud solutions can be integrated, and many organisations still operate this model.
Written by:
Chukwuma Okoli
Consultant