Phishing is a social engineering attack used to steal data, including login credentials and cardholder data. It involves an attacker masquerading as the legitimate entity, deceiving a victim into opening an email, providing a piece of information via telephone calls, instant messages, or text messages.
The origin of Phishing attacks may be attributed to the days of AOL when a group of attackers posing as AOL staff using AOL messenger, asking people to verify their accounts or billing information. Many users, including those within the tech space, still fall prey to this cyber security attack purely due to the ever-changing mechanisms and sophistication. The more internet users decipher the approaches to these attacks, the more the attackers devise new means and become more proficient in luring their victims. More users have started becoming aware of these attack mechanisms through awareness and training and are more prepared to respond to their schemes.
Today, organizations build multiple layers of protection utilizing numerous firewalls and access control technologies, and networks are designed with solid perimeter, demilitarised zones to ensure the organisation’s critical assets are well protected. Attackers find it challenging to break into the firewalls. So instead of spending weeks trying to break into the network by compromising the firewall, an effortless way out will be to tunnel malware over all the layers of network protection or utilize social engineering tools to gain unauthorized access into the network. They must, however, find ways to tunnel this malware into the network by using the different phishing mechanisms.
Phishing has remained the same over the years, and the ideology still utilizes social engineering tactics to lure users and trick them into compromising their information. What has changed and continues to advance is the presentation. Still, in some of the Business Email Compromise cases, you will see the traditional signature of a hurriedly typed email with fake email addresses and occasioned by spelling errors, but recently the presentation has changed, and there has been much improvement in how these attacks are carried out.
Is Phishing a Real Threat?
The year 2020 did not just witness one of the most devastating pandemics; it also saw a rise in Phishing attacks. According to Internet Crime Report (IC3), phishing attacks doubled in 2020. Recent research conducted by Proofpoint indicated that 75% of organizations worldwide experienced a phishing attack in 2020. From the study, despite having 95% of organizations claiming that they have delivered information security awareness training to their staff, phishing remains the threat type most likely to cause a data breach. According to Abnormal security, a 2020 survey showed that the number of business email compromise (BEC) attempts received between Q2 and Q3 increased by 15%. In an IBM report, nearly 22% of companies that reportedly suffered a malicious data breach in 2020 were breached due to lost or stolen credentials. A recent Data Breach Investigation Report (DBIR) by Verizon showed that 36% of breaches involved phishing and is 11% more than that of 2021.
Phishing has evolved, so should you.
The latest trends in phishing attacks have seen the attacks evade detection. Most email security filters will effectively block spam emails from entering the inbox, but we can’t say that about phishing emails. Most phishing emails evade these traditional email filters and go undetected into the mailboxes. Phishing in recent times has employed very sophisticated techniques, allowing them to bypass security filters while making their way into the environment.
Gone are the days when phishing emails were fraught with typos and mistakes. A properly written phishing email is difficult to distinguish from an actual email. In the past, it was common to identify phishing emails bearing attachments with Windows executables (.exe), Script files, and Office documents. Today with the advancements and sophistication in phishing, it has become common to see phishing emails with attachments in PDF formats, Java files, Batch files, and Shortcuts.
There are different methods employed by the latest phishing techniques, so sophisticated and covert that they could bypass Office 365 Exchange online protection security.
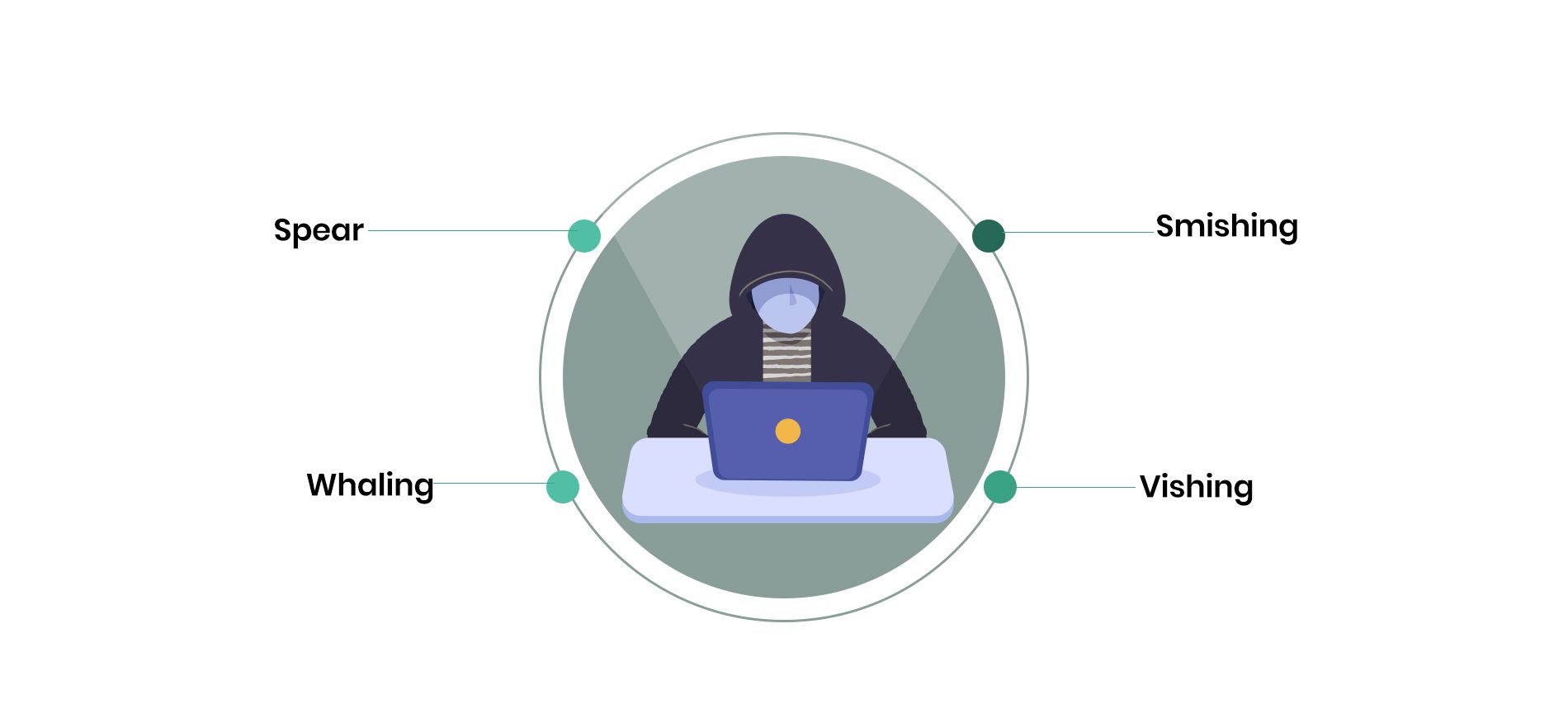
Some of the Phishing methods
Different types of phishing attacks are based on the targets, sometimes. Phishing can have varying marks; some can target specific individuals, while some can target a group of people.
Spear phishing is a type of phishing targeted at an individual, sometimes the system administrators of companies. And, most times, the aim is to compromise the system administrators’ account and harvest it to gain unauthorized privileged level access into the system or trick unsuspecting users that the email originated from the system administrator’s account.
Another form of phishing attack is Whaling. Sometimes catching a big fish makes more sense, right? This type of phishing is targeted at the industry’s C-suites, especially the CEO and CFO. A whaling email might target the C-suite and require them to click on a link to supply some personal information. Others could deceptively originate from the CEO instructing the CFO to make an urgent payment for goods or services to fake entities. In the past, such emails had come with phony email accounts, and when looked at closely, it is easy to decipher a mistake in the email accounts. Either the domain is mistyped, or an entirely different email account is masked under a pseudo email account, but lately, attackers have compromised real email accounts of the victims and used them to send what looks like genuine emails to unsuspecting users.
Smishing is a type of phishing attack that uses text messages known as short message services (SMS) to lure users by inserting links within the messages that users could click. Most times, attackers have sent these messages with some SOS impression asking users to click on the links and supply some vital information to avert a suspension or stop a compromise of their accounts.
The other type of phishing attack is called Vishing. The attack is accomplished through a phone call. The attackers use current mechanisms to evade secure email gateways and Exchange Online protection by inserting legitimate links into the emails. Traditionally, many email gateways scan a number of the inserted legitimate links and assume the email is clean. In other instances, the attackers could mix legitimate connections with malicious ones, and the idea is to evade detection by secure email gateways.
In the past, once you launched a phishing link and input your personal information, the URL either time-out or remains static.
Today most attackers will want to cover their tracks so that their victims will not know that they have been phished by redirecting them to a legitimate page after a successful phishing attack.
Another technique that phishers use to hide phishing URLs is URL shorteners like TinyURL and Bitly. Using URL shorteners masks long URLs with shortened URLs, and most signature-based email filters do have a way to decipher a phishing link from a shortened URL
Building cyber resilience to stay protected
Just as in all instances of information security, a defense-in-depth approach that comprises technical and administrative controls will prove more effective in tackling phishing attacks—deploying secure email gateways, using Artificial Intelligence and machine learning solutions that can scan and analyze each communication and detect abnormal patterns and a combination of the above with regular security awareness training. The best way to start is to conduct an assessment to understand your current state.
Implementing siloed controls has failed to produce the right results. That is why at pcl., we support organizations both in developing and implementing tested Cybersecurity strategies to ensure that organizations can protect their assets while conducting their businesses. Our approach involves understanding the context of your organization, your business objectives, and the factors and risks that could prevent you from achieving your goals.
Our assessment methodologies incorporate both technical and non-technical approaches to understanding your current state. Beyond assessments, we partner with you to navigate from your current state to the future state that will deliver the needed return on security investments. We also provide managed security and assurance functions to ensure that operationally, organizations are well protected against destructive Cybersecurity incidents. Contact us today, send an email to technology@phillipsconsulting.net to start the engagement.
Written by:

Ben Nnatuanya
Senior Consultant